Still on spring break around here. If I was legit on a road trip some place warm right now, you’d find me lounging in the sun, sipping fruity cocktails at all hours, listening to some cheesy exotica like this Arthur Lyman piece I’ve shared here.
Though horribly appropriative and colonialist, it’s hard not to like exotica for its in-your-face corniness. I think my favorite remains Martin Denny’s Quiet Village. It brings back memories from the early 1960s, when life was pretty simple.
Let’s have a mai tai for breakfast and get on with our day.
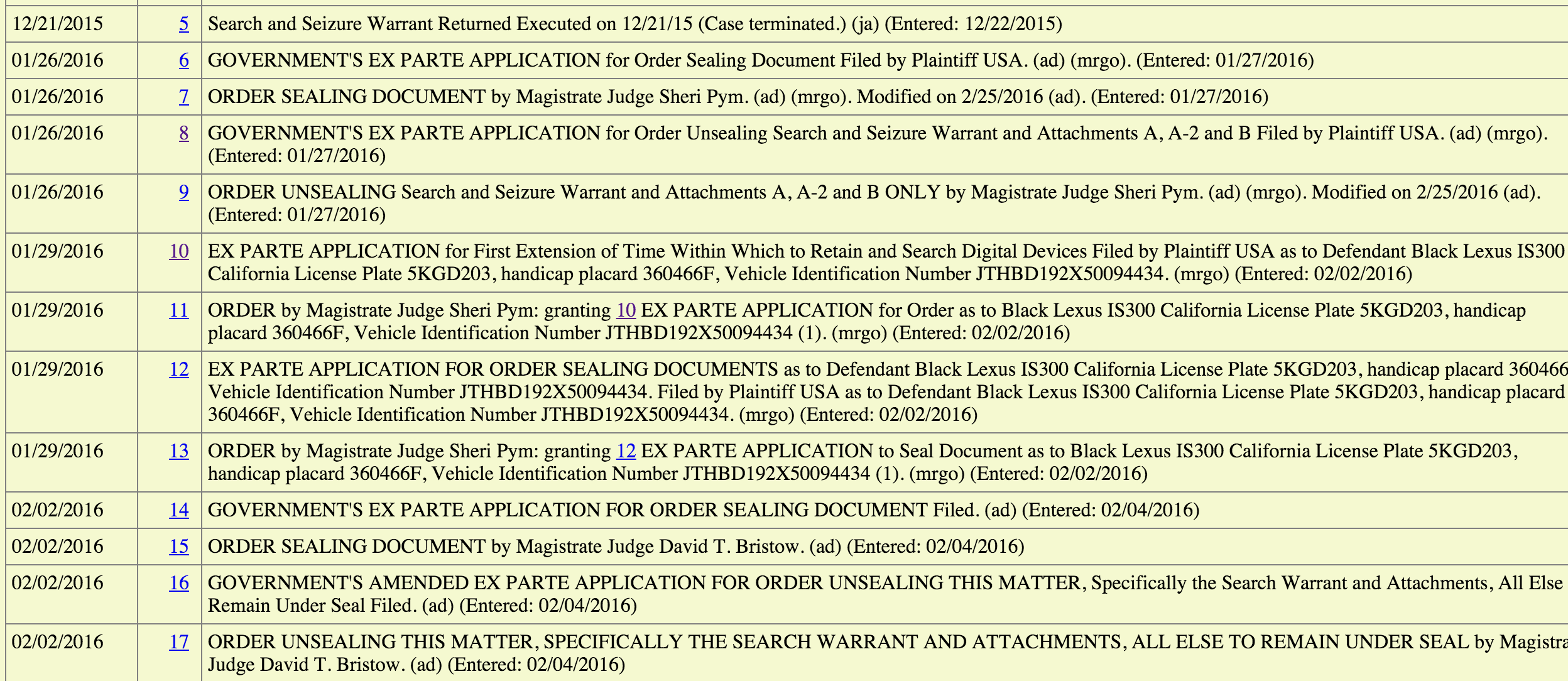
Urgent: Increasing number of hospitals held ransom
Last month it was just one hospital — Hollywood Presbyterian Medical Center paid out bitcoin ransom.
Last week it was three — two Prime Healthcare Management hospitals in California and a Methodist Hospital in Kentucky held hostage.
Now, an entire chain of hospitals has been attacked by ransomware, this time affecting the servers of 10 related facilities in Maryland and Washington DC. The FBI is involved in the case. Is this simple extortion or terrorism? The patients diverted from the facilities to other hospitals’ emergency rooms probably don’t care which it is — this latest attack interfered with getting care as quickly as possible. Let’s hope none of the diverted patients, or those already admitted into the MedStar Union Memorial Hospital chain, have been directly injured by ransomware’s impact on the system.
The MedStar cases spawns many questions:
- Was any patient’s physical health care negatively affected by the ransomware attack?
- Given the risks to human health, why aren’t hospitals better prepared against ransomware?
- Have hospitals across the country treated ransomware as a potential HIPAA violation?
- Was MedStar targeted because of its proximity to Washington DC?
- Was Hollywood Presbyterian Medical Center targeted because its owner, CHA Medical Center, is South Korean?
- Were any patients being treated at MedStar also affected by the OPM data breach, or other health insurance data breaches?
- How much will ransomware affect U.S. healthcare costs this year and next?
Bet you can think of a couple more questions, too, maybe more than a couple after reading this:
Hospitals are considered critical infrastructure, but unless patient data is impacted there is no requirement to disclose such hackings even if operations are disrupted.
Computer security of the hospital industry is generally regarded as poor, and the federal Health and Human Services Department regularly publishes a list of health care providers that have been hacked with patient information stolen. The agency said Monday it was aware of the MedStar incident.
Apple iPhone cases emerge
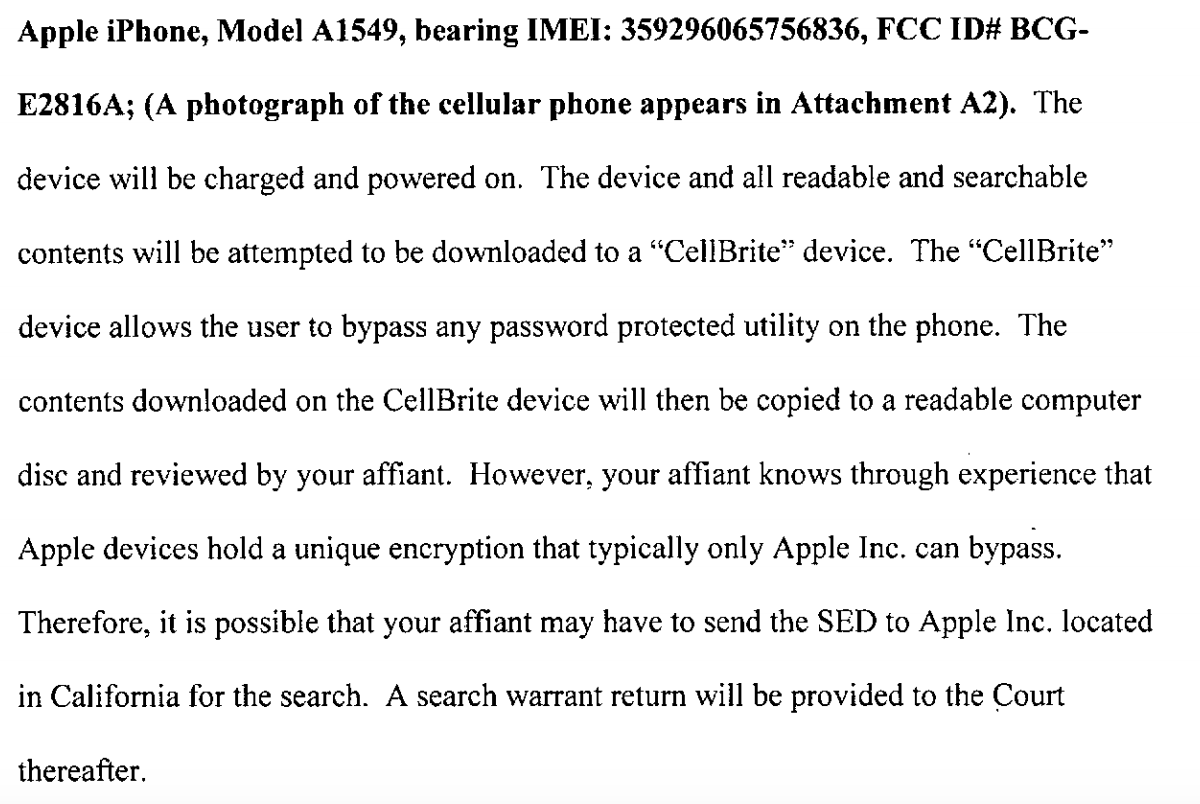
After the San Bernardino #AppleVsFBI case, more law enforcement investigations relying on iPhones are surfacing in the media.
- L.A. police crack open iPhone with fingerprints obtained under warrant (Forbes);
- FBI will assist county prosecutor in Arkansas with iPhone belonging to alleged teen killer (Los Angeles Times); the method may be the same hack used on the San Bernardino phone, which was supposed to be a one-off (Network World);
- ACLU found 63 other cases in which FBI used All Writs Act to obtain iPhone/Android smartphone data from Apple and Google (The Register).
Stupid stuff
- In spite of screwing up not once but twice by releasing its racist, obnoxious Tay AI chatbot, Microsoft tripled down on a future full of chatbots you can build yourself with their tools. (Ars Technica) — Ugh. The stupid…
- UK’s Ministry of Defense awarded funding to Massive Analytics for work on “Artificial precognition and decision-making support for persistent surveillance-based tactical support” (Gov.UK) — OMG Precog in warfare. Human-free drone attacks. What could go wrong?
- Rich white guys queue up outside Tesla dealerships for days waiting to pre-order the new Tesla 3 (Vancity Buzz) — Vancouver, Sydney, probably other places I’m too arsed to bother with, because rich white guys.
That’s quite enough. Back to pretending I’m lying under a cerulean sky, baking my tuchis, cold drink in hand.